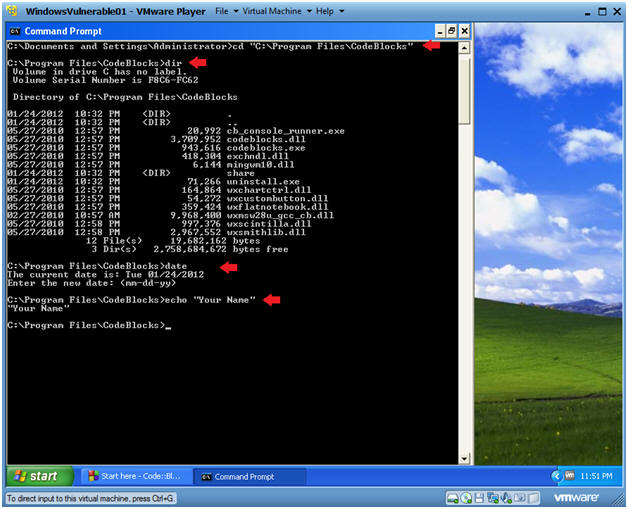
Trojan horse code top
Trojan horse code top, Trojan Horse Meaning Examples Prevention top
4.75 (1244)
Limited-Time Special
$38.99 (50% off) $77.98
Color:
Size: Please select
Product Details
Web ID: 1371
How To Get Rid of a Trojan Virus Malware Computer virus Trojan top, Trojan Horse With Binary Code Isolated Stock Photo Download top, Trojan horse computer Stock Photos Royalty Free Trojan horse top, Cyber Security Community of SLIIT Are you aware about Trojans top, A Trojan virus infected digital source code. 3D illustration Stock top, Computer Hacker Code Java Trojan Virus Network Programming Language top, How to Tell if Your Computer Is Infected by a Trojan Horse top, In version 1.1.1 a Trojan horse is detected by Windows Defender top, RIP Copy and Paste from Stackoverflow Trojan Source Solution top, How to Create a Trojan Virus in Kali Linux Live Linux USB top, backdoor trojan virus Penetration Testing Lab top, Computer virus top, Cyber Attack Translation Trojan Horse Vulnerability Stock top, Android Trojan Horse top, Dvmap the first Android malware with code injection Securelist top, Trojan Malware Unveiled All You Need to Know to Stay Safe top, How to Create a Trojan Virus in Kali Linux Live Linux USB top, Binary Code Trojan Virus On Black Stock Illustration 308059352 top, Trojan Malware What is a Trojan Virus IDStrong top, Trojan Virus Quiz. Trojan Quiz by Examsegg Medium top, C homework trojan found when compiling the code Stack Overflow top, What is the Trojan Horse Virus SYSNETTECH Solutions top, Placeholder Trojan Writing a Malware Software top, Trojan Source attack method can hide bugs into open source code top, Trojan Horse 1 Lesson 1 Install a C C Compiler top, Trojan horse code composition Royalty Free Vector Image top, How to protect yourself against Trojan Source unicode attacks with top, Trojan horse conceptual image of Trojan malware computer virus top, Trojan Horse Meaning Examples Prevention top, Trojan Source attack method can hide bugs into open source code top, Trojan Horse Virus Examples How to Defend Yourself top, Python Trojan undetectable . I am going to be showing you how to top, Trojan Horse 2 Lesson 1 How to create and bundle the metasploit top, Trojan Horse Embedded codes Person of Interest Wiki Fandom top, Computer Code Says Trojan Horse Stock Photo 641039281 Shutterstock top, Product Info: Trojan horse code top
.
.